2023年のWordPressセキュリティの現状
課題は、2023 年の WordPress セキュリティの進化し続ける状態であり、最新のサイバー脅威から保護することです。
WordPress has been a popular website CMS platform since its inception in 2003. However, with popularity comes the risk of security threats. As we enter 2023, it’s essential to take stock of the current state of WordPress security.
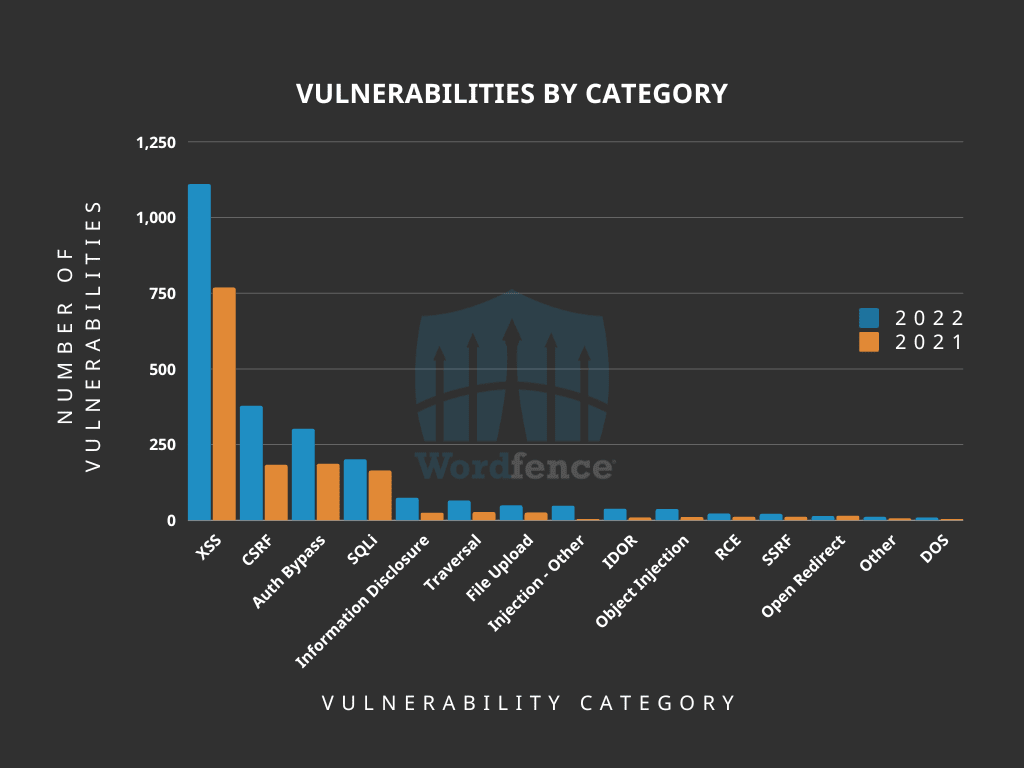
WordPressのセキュリティ脆弱性のカテゴリ別
画像ソース: ワードフェンス
2021年から2022年の間に、開示された脆弱性の上位5つのカテゴリに大きな変化が起こりました。注目すべき変化の 1 つは、情報漏えいがファイルのアップロードを上回り、5 番目に多い脆弱性カテゴリになったことです。これは、機密データや機密データを保護することの重要性を浮き彫りにしています。さらに、CSRFの脆弱性は大幅に増加しており、2021年から2022年にかけてほぼ倍増した認可バイパスの脆弱性よりも高い位置を占めています。
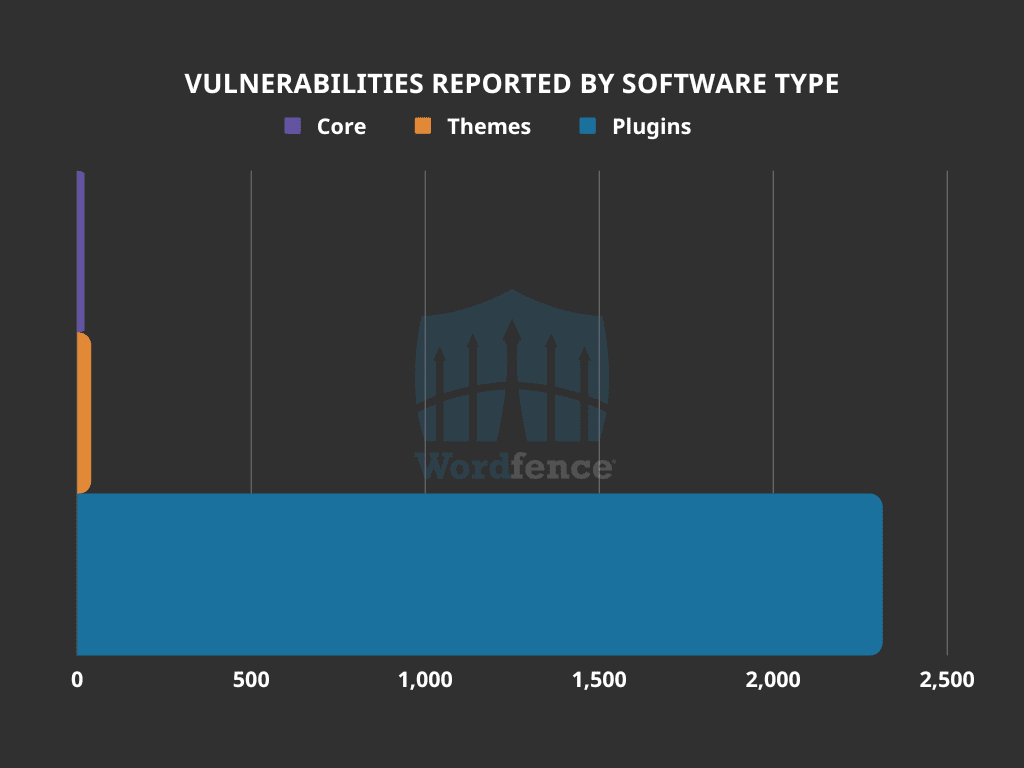
WordPressのセキュリティ脆弱性(ソフトウェアタイプ別)
画像ソース: ワードフェンス
Examining the distribution of where vulnerabilities were reported, it is evident that plugins comprise the overwhelming majority of reported vulnerabilities. It’s important to acknowledge that there are considerably more plugins than themes available, which naturally influences this statistic. Nonetheless, this emphasizes that the WordPress core platform is comparatively more secure, and any security concerns in the WordPress ecosystem may be attributed to plugins and themes.
ここでは、WordPressのセキュリティ統計を簡単に紹介しますので、以下で詳しく説明します:
- ハッキングされたWordPressサイトの74%は、攻撃時に古いソフトウェアを使用していました。
- 最も人気のあるWordPressサイトのプールのうち、26のサイトには重大なセキュリティリスクを伴うプラグインがありました。
- 2022年には、セキュリティ関連のバグが前年より328件多く報告され、総数は4,528件になりました
長年にわたってセキュリティを向上させるための多くの努力にもかかわらず、WordPress は古いソフトウェア バージョンと脆弱なパスワードによる攻撃に対して依然として脆弱です。実際、Sucuriのレポートによると、ハッキングされたWordPressサイトのほぼ74%が、攻撃時に古いソフトウェアを使用していました。さらに、プラグインやテーマは定期的に更新しないと潜在的な脆弱性が生じます。
そうは言っても、近年、WordPress のセキュリティ強化に向けて顕著な改善が行われています。これらには、コアファイルの自動更新が含まれます。 プラグインと改善 ユーザーパスワードの要件。
この事実を考えてみましょう: 2022 年に、人気のある Web サイト プラグインのセキュリティに関して衝撃的な発見が行われました。これらのプラグインのうち 26 には、パッチが適用されなかった重大なセキュリティ バグが含まれていることが判明しました。これらのプラグインを実行している Web サイトは、ハッキングされ、機密情報が侵害される危険があります。
This revelation proves website owners cannot afford to be complacent regarding their sites’ security. With cyber threats growing more sophisticated daily, businesses must take all necessary steps to protect themselves and their customers. This includes regularly updating software and ensuring that any vulnerabilities are quickly addressed.
2022年には、WordPressプラグインのセキュリティバグレポートが大幅に増加しました。具体的には、前年より328件多いバグが報告され、データベースで確認されたセキュリティバグの総数は4,528件となりました。これは、わずか1,382件のセキュリティバグが報告された2021年よりもはるかに大幅な増加でした。これらの数字は、プラグインのセキュリティ脆弱性を定期的に監視し、できるだけ早く更新することの重要性を示しています。
As one of the world’s most popular content management systems (CMS), WordPress is often targeted by cybercriminals seeking to exploit vulnerabilities in the platform’s code. WordPress has implemented several security measures to counter this threat over the years, including automatic updates and improved password policies. However, responsible disclosure is one of the most effective ways to make the WordPress ecosystem more secure.
近年、責任ある開示がより一般的になってきており、WordPress エコシステムはこの傾向から大きな恩恵を受けています。多い 脆弱性を発見するセキュリティ研究者 WordPressプラグイン、テーマ、またはコアプラットフォームでは、WordPressセキュリティチームに報告することを選択し、プラグインやテーマの開発者と協力してパッチをリリースできます。
責任ある開示の利点の 1 つは、開発者が 脆弱性の修正 広く知られるようになる前に。これは、サイバー犯罪者が この脆弱性を悪用して WordPress サイトを侵害する . When vulnerabilities are publicly disclosed before a fix is available, this is known as “zero-day” exploitation.
責任ある開示により、WordPress ユーザーは脆弱性にタイムリーにパッチを適用できるため、サイトがハッキングされるリスクが軽減されます。脆弱性が発見され、責任ある開示を通じて報告された場合、WordPress セキュリティ チームは迅速にパッチをリリースできます。サイト所有者は、プラグイン、テーマ、またはWordPressコアプラットフォームを更新してパッチを適用し、サイトが侵害されるリスクを軽減できます。
WordPress コミュニティは責任ある開示の重要性を認識しており、現在いくつかの取り組みがこの実践を促進しています。たとえば、WordPress セキュリティ チームには、セキュリティ研究者が脆弱性を報告するための専用の電子メール アドレスがあります。現在、多くのプラグインやテーマの開発者は、ウェブサイトに責任ある開示ポリシーを盛り込んでいます。
結論として、責任ある開示は、WordPress エコシステムのセキュリティを強化するために不可欠な実践です。セキュリティ研究者は、責任を持って倫理的に脆弱性を WordPress セキュリティ チームに責任を持って倫理的に報告することで、開発者がパッチを迅速にリリースできるように支援し、ゼロデイ悪用のリスクを軽減できます。WordPress ユーザーは、サイトにタイムリーにパッチを適用することで責任ある開示の恩恵を受け、サイトが侵害されるリスクを軽減することもできます。WordPress コミュニティは、プラットフォームが何年にもわたって安全で信頼できる状態を維持できるように、責任ある開示を促進し、奨励し続ける必要があります。